In this second installment of our three-part analysis of the Proxmark3 RDV4 and the ProxmarkPro, we will be examining the hardware performance of each device with respect to reading, writing, and emulating RFID cards in the field. This series of tests will include determining the maximum range for each of the device’s default and add-on antenna modules across a wide-spectrum of RFID tag types, as well a heads-up comparison of card-side attacks against four different RFID entry systems. Though there are many factors that determine the value of a tool, the raw metrics collected and presented in this article is the most relevant to assessing the efficiency and flexibility of each device in the field.
As identified in the previous article, the ProxPro by Rysc Corp and the PM3 RDV4 by RFID Research Group have taken diametrically opposed paths to delivering a field-capable, standalone RFID tool for researchers and redteamers. The ProxmarkPro includes an onboard UI that provides a stripped-down version of the client, with a few dozen functions selectable via the device’s navigation buttons. Although this provides the user with several out-of-the-box functions and eliminates much of the learning curve associated with the Proxmark3, it does so at the sacrifice of customization and with a much narrower range of target cards and attack options than other variants on the market. The RDV4 on the other hand, provides its user with full client functionality via bluetooth connection to your android device and the RFID Tools App. Interacting with the client requires a much higher level of experience with the PM3 before being ready for the field, but it does allow the user to access the entire suite of functionality currently available through the various firmware forks in the open-source development community.
How will these different approaches to development effect the performance of each device in the field? Let’s dive into the data to find out.
Disclaimer/Conflict of Interest
It should be noted that the we, the conductors of this research and writers of this article, are affiliated with RFID Research Group (RRG) as exclusive distributors of the Proxmark3 RDV4 in North America and that Rysc Corp (RC) is a direct competitor in the info sec device retail market. That said, the aim of this article is to provide an objective analysis of the above mentioned device’s capabilities based on accurate measurement, thoughtful consideration, and above all, an honest representation of the facts and data collected herein. It is our hope that the information presented in this article will help those in our community interested in RFID technology make a more informed choice when purchasing their Proxmark3, no matter what device they choose or who they purchase that device from.
Field Utility Trials
One of the primary metrics of hardware performance for any Proxmark3 is going to be the maximum range of a successful card read. This is especially true for any device intended for use in the field, where you are not likely to have physical possession of the target card. Most common attacks are performed on the card side of the system and the greater the distance your device will be able to read this card from, the more options you will have in an actual engagement.
Both the ProxmarkPro and the Proxmark3 RDV4 are designed with interchangeable antenna sets to customize the device for your target RFID cards and readers. Each manufacturer lists maximum read ranges for each of their antennas, but with the sheer diversity of tag types and manufacturers in the wild, these figures cannot be taken at face value. To test the true range of each device, we used 23 different commercial and consumer RFID tags and measured the maximum reading distance for each of the nine device/antenna combinations.
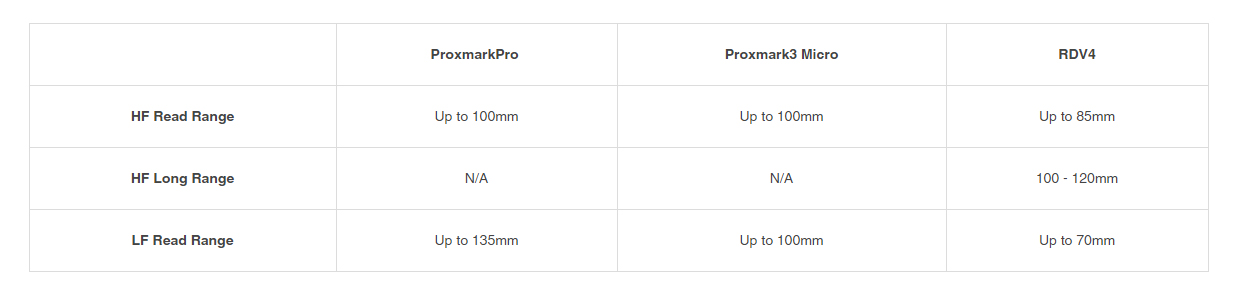
Figure 1 A - ProxmarkPro Official Antenna Range Published by Rysc Corp
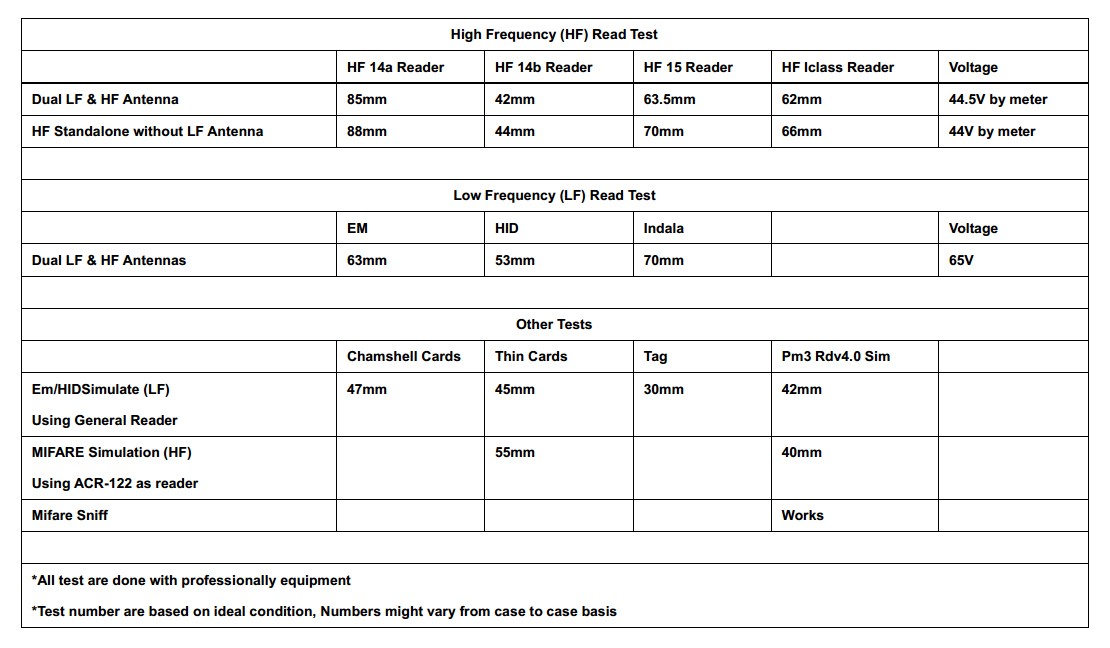
Figure 1 B - Proxmark3 RDV4 Official Antenna Range Published by Proxgrind
In addition to the antenna load-out detailed in the first article, we performed the same test on each of the default LF and HF antennas included in the ProxmarkPro kit, as well as the 5 different modular antennas currently available for the RDV4. For more information about these accessory antennas by RRG and a walk-though on installation, check out our Proxmark3 RDV4 Hardware and Accessories Guide.
Test Parameters
Measurements were taken in inches for each target RFID tag, moving the tag in 1/8 inch increments starting at 8 inches from the antenna. For the Proxmark Pro, the Identify command was issued at each increment. For the RDV4, the LF Search or HF Search easy buttons were sent at each increment using the RFID Tools Android App. Each read attempt was made allowing the command to fully cycle, moving the card closer for each attempt until a successful read was completed. Reads were only considered successful if the correct card ID and card type were retrieved by the device. This process was repeated 10 times for each tag/antenna combination, throwing out the highest and lowest values and averaging out the remaining 8 measurements to the nearest 1/8 inch. RFID tags and antennas were held in the same plane, perpendicular from a ruler, rotating the antenna by a few degrees in the vertical axis during each read attempt.
The 23 different RFID tags were chosen from a collection of blank cards purchased from a commercial supplier, test cards from the ProxmarkPro and RDV4 kits, as well as consumer grade tags, an implantable RFID bio chip, and old hotel room key cards. These represent a wide spectrum of the common RFID tag types in the wild with varying degrees of security implementation.

Figure 2 A - ProxmarkPro in Antenna Read Range Test

Figure 2 B - Proxmark3 RDV4 in Antenna Read Range Test
Hybrid Antenna Comparison
Looking at the hybrid LF and HF antenna results for each of the devices, we can see that there is a clear trend in longer read range in HF cards for the RDV4, with the ProxPro demonstrating greater range in LF cards. To quantify the difference in performance across the data collected, we calculated the percentage change between the values for each device and then averaged out the deltas by HF and LF card type. The resulting data shows a 10.6% increase in range for HF cards using the RDV4. The difference in range was significantly greater in the LF cards tested, with the ProxmarkPro performing at an average of 84.8% greater distances – and in the case of the EM4100 commercial key fob, the ProxPro more than tripled the read range.
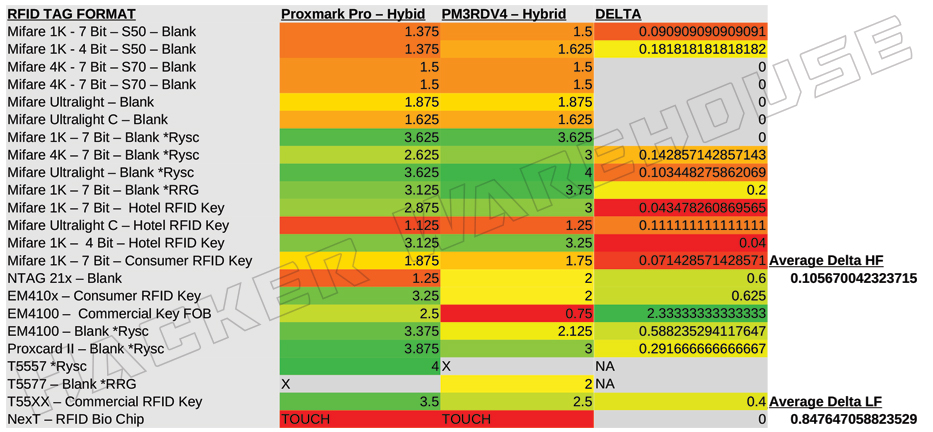
Figure 3 - Proxmark3 RDV4 and ProxmarkPro Hybrid Antenna Range in Inches
The deltas in performance between these two hybrid antennas may seem significant, but when you take into consideration the actual scale of these distances, the difference is effectively negligible. For most of these cards, the increased range rarely exceeds a fraction of an inch for either device. The largest increase in raw physical range was a mere 1.75 inches – a few finger-widths at best.In a live engagement, the additional range is unlikely to provide any real advantage to the user when considering the extremely close proximity one needs to have with the respect to the target card, whether located on a person or not.
LF Antennas
When looking at the frequency-range specific antennas, however, we do start to see some tactically significant distances in the read range of each device. Staring with the ProxmarkPro’s dedicated LF antenna, which improves its performance over the RDV4 hybrid antenna to a whopping 106.3% (meaning more than twice the range on average). This includes an impressive 6 inches for the T55xx commercial RFID key that we tested – which can mean the difference between having to invade a target’s personal space or not when attempting to get that successful read. It should be noted that the LF antenna is significantly larger than the ProxmarkPro’s hybrid, further increasing the visibility of the device.
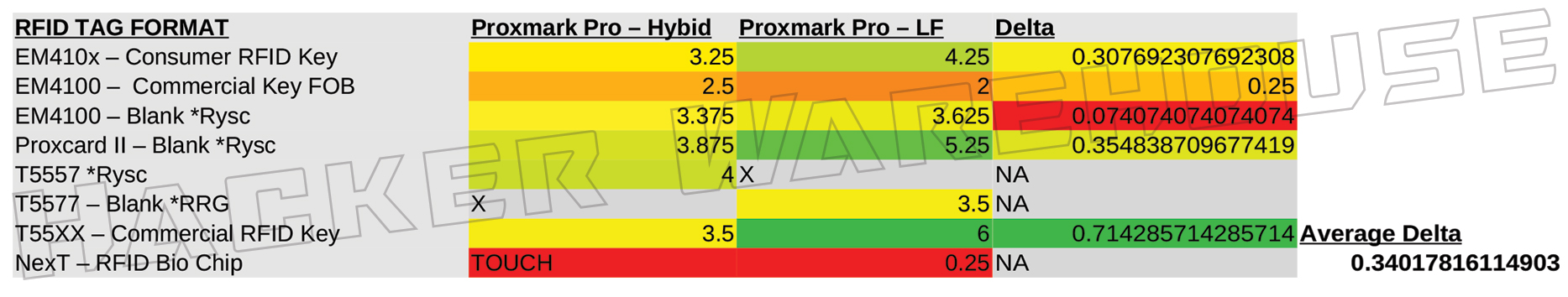
Figure 4 - ProxmarkPro Hybird Antenna vs LF Antenna Range in Inches
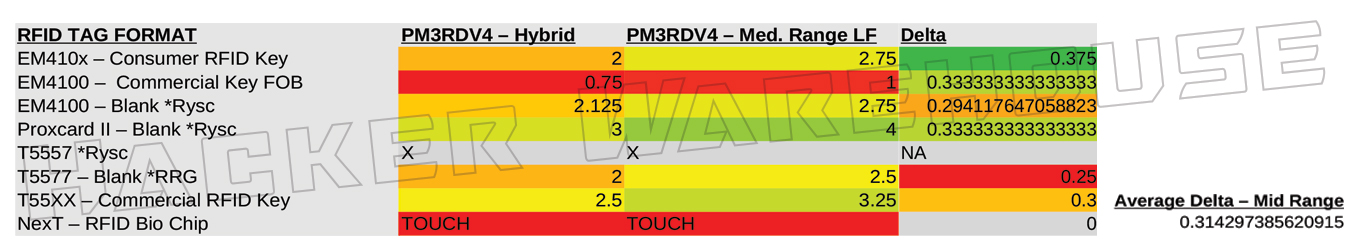
Figure 5 A - Proxmark3 RDV4 Hybrid Antenna vs Medium Range LF Antenna Range in Inches
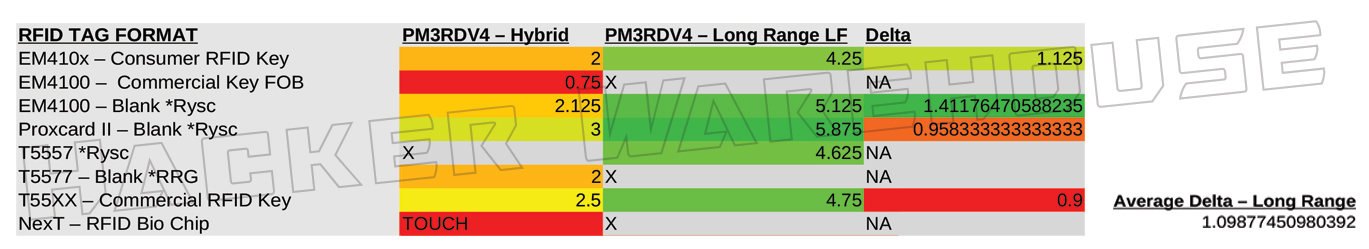
Figure 5 B - Proxmark3 RDV4 Hybrid Antenna vs Long Range LF Antenna Range in Inches
This advantage persists even when comparing it to the ranges of the RDV4’s dedicated medium range and long range LF antennas. Surprisingly, the medium range antenna by RRG only provides an average of 31.4% greater distance over the default hybrid antenna included with the device – even with the Q value switch set to 14 for increased range. The long range antenna by RRG does start to close the gap with an average of 109.8% improvement over the RDV4 hybrid and some read ranges extending past 4 inches. It was even able to beat the ProxPro’s dedicated LF antenna with 2 of the cards tested (ironically, these cards were both from RC). That said, the long range antenna was temperamental in use and was much more difficult to obtain a read on most cards, as well as having the highest rate of non-detection among all the antennas tested here.
HF Antennas
Just as the ProxPro continued to trend better with LF cards, the RDV4 increases its advantage in the HF range when using its dedicated HF antennas. The medium range HF antenna only provides a slight 7.8% improvement over the default hybrid antenna, roughly doubling its performance over the ProxPro’s hybrid antenna and taking a small advantage over the dedicated HF antenna. When outfitted with the long range antenna however, the RDV4 more than doubles the average range as the ProxPro in HF cards, allowing for successful reads of Mifare 1K, 4K, and UL at up to 6.25 inches. Just as noted with the ProxmarkPro’s dedicated LF antenna, both variants of the long range antennas for the PM3 RDV4 does increase the physical dimensions of the device significantly, with potential effects on covert use of the device.
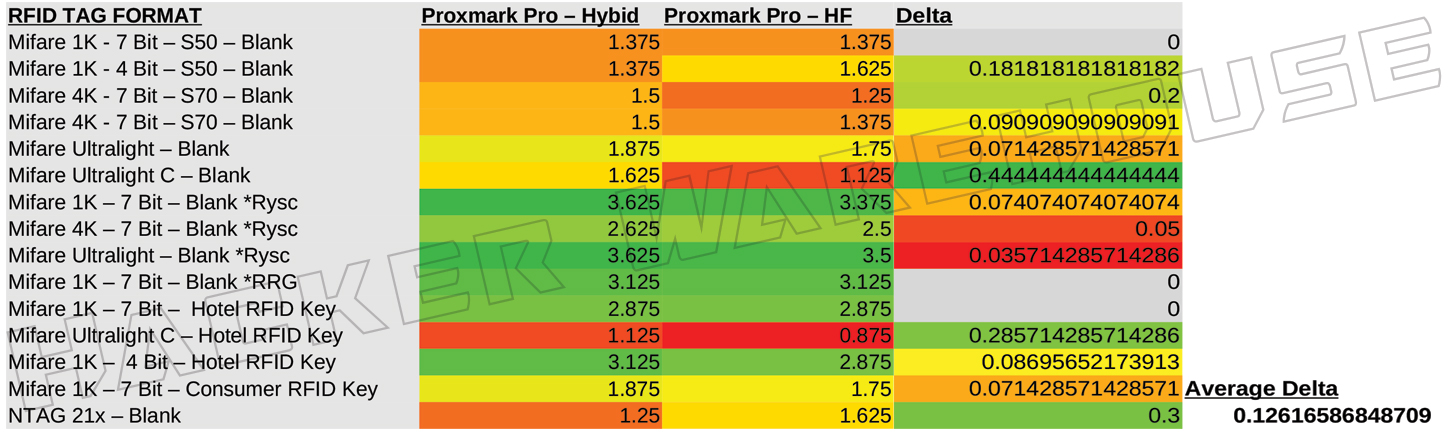
Figure 6 - ProxmarkPro Hybird Antenna vs HF Antenna Range in Inches
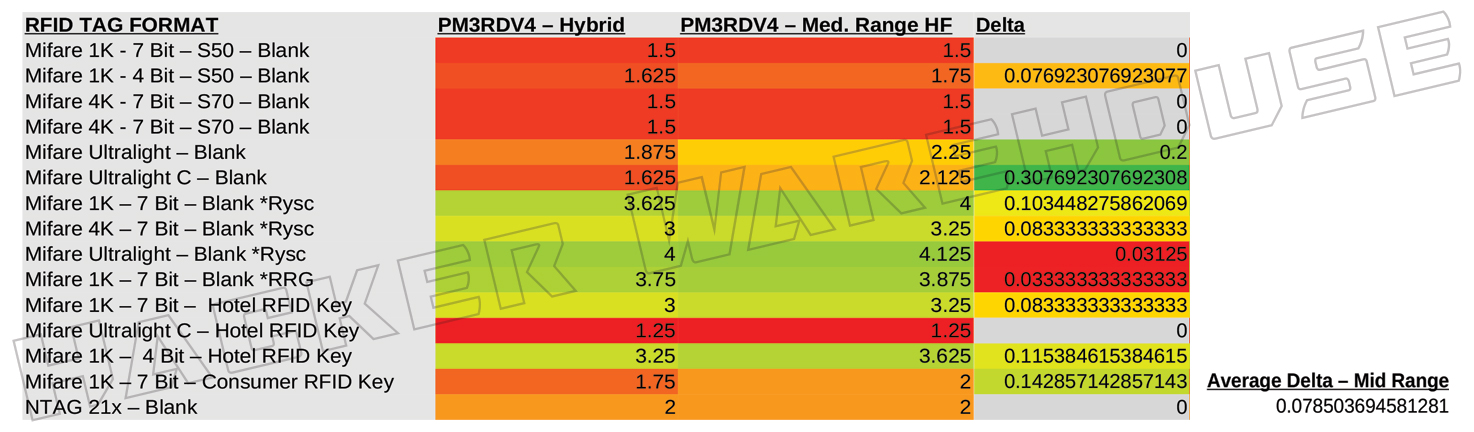
Figure 7 A - Proxmark3 RDV4 Hybrid Antenna vs Medium Range HF Antenna Range in Inches
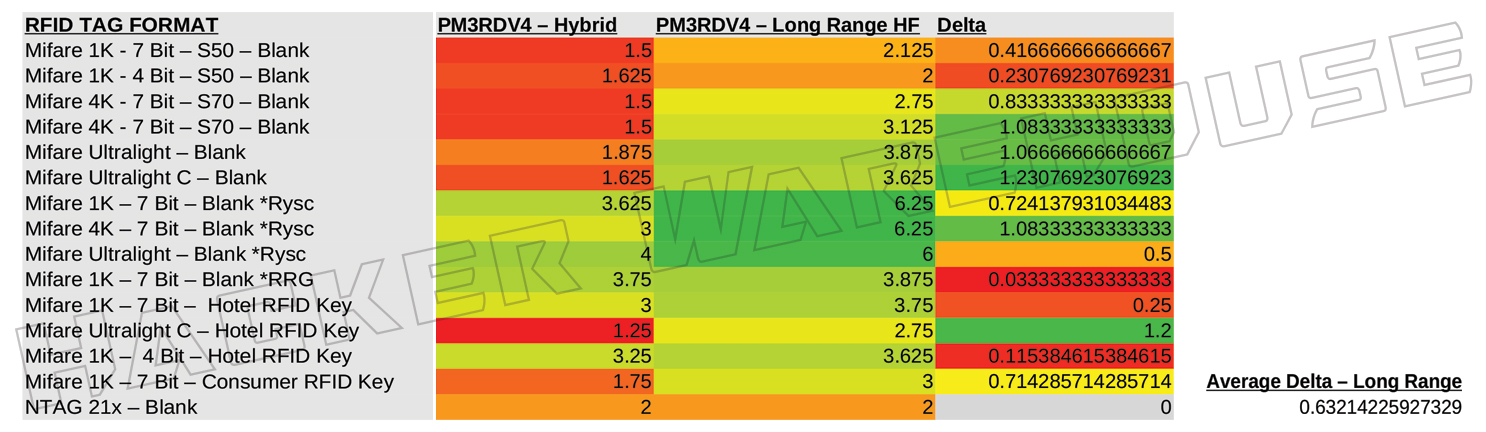
Figure 7 B - Proxmark3 RDV4 Hybrid Antenna vs Long Range HF Antenna Range in Inches
Oddly, the dedicated HF antenna included with the ProxmarkPro kit performs lower than the hybrid antenna across the cards that we sampled in this test. On average, the antenna’s range was 12.6% shorter than that of the hybrid. I had assumed that these antennas contained the same hardware for HF given the near identical size and traces of the boards, so this difference in performance may reflect manufacturing tolerances. The hybrid antenna is a more recent product than the dedicated ones, so this improved range might be the product of better design or manufacturing capability.
LF Ferrite Bio Chip Antenna
As expected, the Ferrite LF antenna for the RDV4 was unable to read any of the tags any further away than physical contact with the reader. This antenna is specifically designed for use with bio-implant RFID chips such as the ones offered by Dangerous Things – for more information about using the Proxmark3 RDV4 with the Ferrite antenna to read and write to you implantable RFID chip, check out our knowledge base. Needless to say, this antenna provides little utility in the field and is really on suitable for the lab or bio-hacking enthusiasts.
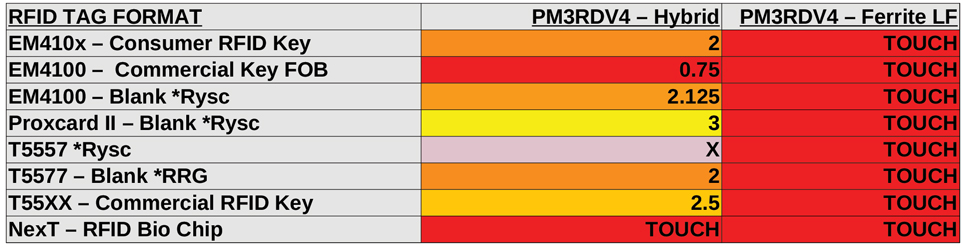
Figure 8 - Proxmark3 RDV4 Hybrid Antenna vs Ferrite LF Antenna Range in Inches
Analysis
When looking at the raw data, it is very easy to determine which device has the longer reading range in each card type and frequency range: the Proxmark3 RDV4 performs at greater distances in HF RFID tags, while the ProxmarkPro tends to do better in LF tags. This is especially true with the hybrid antenna load-out in each device, although the gap disappears when equipping the RDV4 with either the LF or HF long-range antenna variant. In both cases, the long-range antennas demonstrated longer read ranges than the dedicated antennas of the ProxPro.
The deltas in performance may indicate significant performance improvement when looking at the data from this lens, but keep in mind the scale of distances these values represent. With the average difference in read range reflecting less than an inch in gained distance, the effective range between the two devices is practically equivalent. In most deployment scenarios, the device is going to need to be within the personal space of the holder of the target card.
ProxPro
Due to the close proximity required to acquire a valid read on the card, the ability to use the device unobserved becomes crucial. The ProxmarkPro already has a slight disadvantage in this sense, given its larger form factor and exposed antennas boards, but the fact that the device requires interaction with it’s onboard navigation buttons and LCD display essentially mandates that the device be visible to the user during the entire read process. Moreover, the clunky and conspicuous aesthetic of the ProxPro makes it even more difficult to be used unnoticed and may draw the attention of security if seen. This poses an extreme limitation in tactical options when attempting to capture card data in the field.
PM3 RDV4
The Proxmark3 RDV4 instead can be used wireless without physical interaction with the device, being able to send commands and verify success from a standard android device. The RDV4 itself can be hidden on someone’s person or in the surrounding environment, with the user somewhere out of sight or otherwise unnoticed. Being able to separate the actions of getting the device in range of the target from getting a read on and further attacking the card allows for greater flexibility in live engagements.
In short, the difference in read ranges between the devices can be relevant in some cases, but in general are not significant enough to really determine the advantage. The take away from this data should be that both the RDV4 and the ProxPro will require very close proximity to the target card, and that the ability to effectively and covertly use the device at this range is the real deciding factor. However, antenna range, form factor, and device UI are not the only variables in this equation – we must also know how long it takes to successfully perform a read on the card to adequately assess field capability.
Back To Field UtilityIn order to assess raw device performance with respect to quickly and effectively performing RFID attacks in the field, we will assume unrestricted physical proximity to the target card and unrestricted access to the target reader. Although this is unlikely to be the case in a live engagement, it is the only way to directly compare the efficacy of the ProxPro and RDV4’s different approaches to delivering standalone functionality in the field.
Our target cards and readers consist of 4 different RFID entry systems: one low-end consumer LF system utilizing generic EM4100 cards; one high-end consumer HF system with custom manufactured Mifare 1K key fobs; one low-end commercial LF utilizing EM4100 cards; and one low-end commercial HF system utilizing hardened Mifare 1K cards. This set of RFID systems was built for practicing attack techniques and general research purposes, and although not specifically designed with complete range of card types in mind, it will be suitable for testing a majority of the functions available to the ProxmarkPro for the sake of comparison.

Figure 9 A - Proxmark3 RDV4 vs ProxmarkPro RFID Access Lab

Figure 9 B - Proxmark3 RDV4 vs ProxmarkPro LF Lock System 1

Figure 9 C - Proxmark3 RDV4 vs ProxmarkPro LF Lock System 2

Figure 9 D - Proxmark3 RDV4 vs ProxmarkPro HF Lock System 1

Figure 9 E - Proxmark3 RDV4 vs ProxmarkPro HF Lock System 2
Basic card-side attack techniques require a work flow that includes identifying the target card’s type, reading the card’s accessible data, and emulating the card data with the device itself or writing it to a blank card. Five individual tests were conducted with each of the four RFID systems in our array to measure time taken to complete both the individual functions and the entire workflow of an emulation attack. For each test, at least 10 trial attempts were made on each device to practice the different inputs before conducting timed runs. From there, five attempts were made for each device per test with only the lowest value recorded – this was done to assume the best case scenario with respect to familiarity with and accurate use of the device.
Identifying a Target Card
The process of identifying a target card is an essential first step, as the RFID tag type dictates how proceed with the rest of the attack. In the case of the ProxmarkPro, the results displayed inform the user which segment of the menu to navigate to for the remainder of the interaction with the target card. Similarly, there are different commands sent via the client terminal to the Proxmark3 RDV4 depending on the target card type and must be manually input for the most part. The RFID Tools app does provide a few pre-programmed “easy-buttons” that make many common actions accessible at the tap of a button.
Video Clip 1 – Side-by-side video of Identify

Figure 10 - ProxmarkPro and Proxmark3 RDV4 Card Identify Time Chart

Figure 11 A - ProxmarkPro Card Identify Display Reading in Unchained Mode
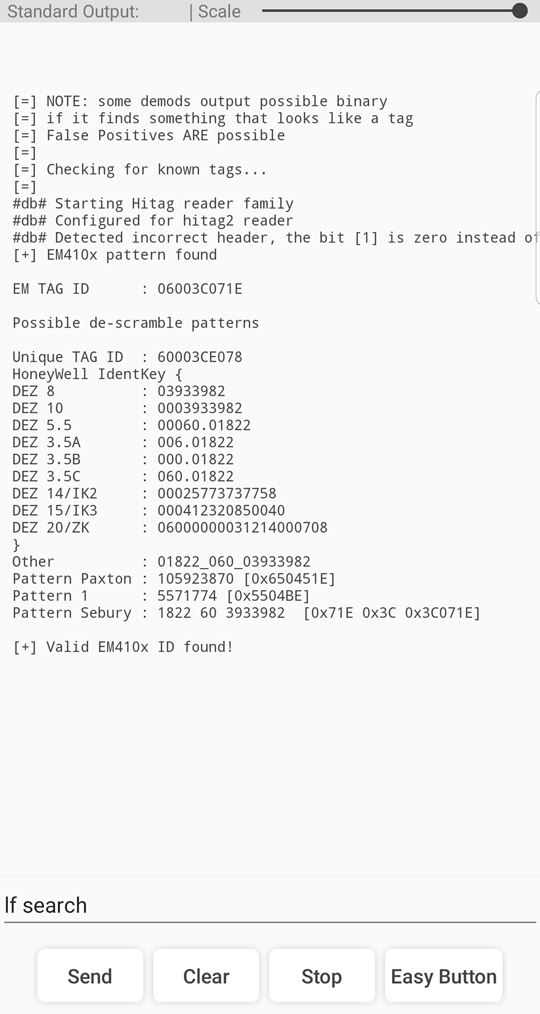
Figure 11 B - Proxmark3 RDV4 Card Identify Client Input/Output via Android App
For both devices, you will need to choose the appropriate frequency range for the function – for the sake of simplicity, we will assume prior knowledge as to whether the card is LF or HF, but will not assume the format of the card. On the ProxPro, it takes 2 button pushes to initiate the identify function for LF cards and 3 pushes for HF cards through the nav menu. This process works out to an average of 3.25 seconds to successfully identify each card, which is confirmed by the LCD displaying the card type and the UID if accessible.
Even though there is an easy button for both HF and LF search functions, the PM3 RDV4 took roughly twice as long to complete a successful card identification – averaging out at 6.17 seconds. When comparing some of the playback footage from the lab, it does seem the command executed a fraction of a second faster than with the ProxmarkPro, but the client does take longer to begin it’s print out. Looking at figure 10 A and 10 B, we can see that we are given considerably more information about the card, consisting of a richer set of diagnostic values to help the user further identify potential vulnerabilities and attack options.
Considering the close proximity required by card-side attacks, combined with the relatively narrow range of orientation to get an accurate read, every second of exposure to the target can be significant. The highly simplified UI of the ProxmarkPro along with the abbreviated identification function does provide the user with a 3 second edge over the RDV4 with respect to raw speed of card identification.
Reading a Target Card
While the process of identifying a target card does provide us with some useful information, the function of reading a card’s data varies across RFID tag types and is a requisite step in emulating or cloning. When using the RDV4 through the client terminal, the user will need to know how to execute the commands specific to that tag type. Although this does require familiarity with the device, the help file available via the terminal is very robust and provides examples of implementation to help you deduce the workflows. This aspect of using the Proxmark3 is beyond the scope of this article, however the exact input commands and output is documented in the screen captures of figure 13 B.
Video Clip 2 – Side-by-side video of Read

Figure 12 - ProxmarkPro and Proxmark3 RDV4 Card Read Time Chart

Figure 13 A - ProxmarkPro Card Read Display Reading in Unchained Mode
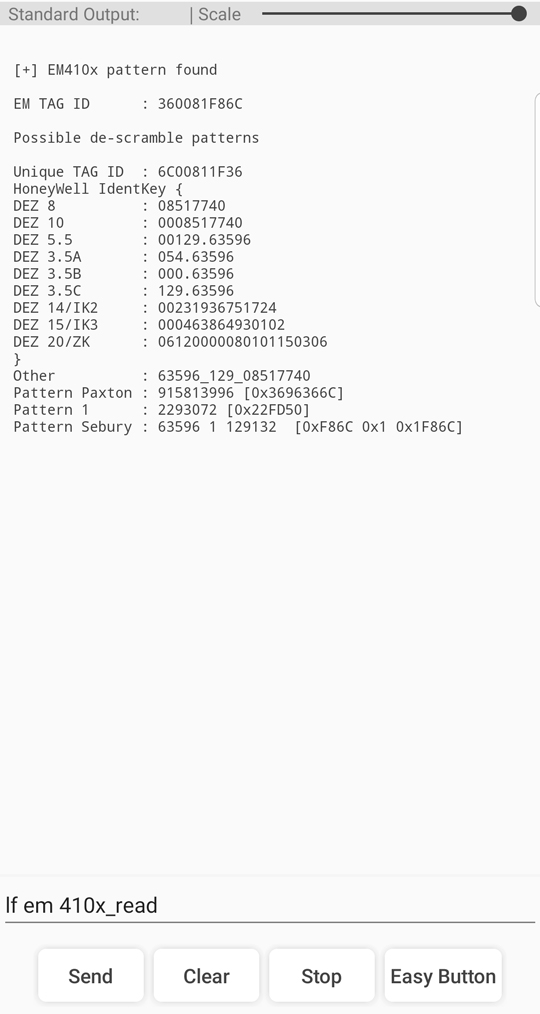
Figure 13 B - Proxmark3 RDV4 Card Read Client Input/Output via Android App
With the ProxmarkPro, the process of reading each card has been simplified to a series of button pushes. Even though the device itself is essentially running the same read functions for each card type as the RDV4, accessing these functions are standardized across the range of the device. The ease-of-use of the ProxPro equates to only a negligible increase in duration to perform a read, this being due to four or five button selections before execution, while HF cards require six. With an average of 4.5 seconds to read each card, simplicity again results in faster performance.
Although there is a slight increase in the length of time required to read a card using the RDV4 over identification, the process can still be accomplished through a single command line. It took an average of 7.5 seconds to successfully read the card data from each of our four targets. Quick typing, auto-fill suggestions, and pre-programmed custom easy buttons can help minimize input time when issuing commands significantly, although all commands issued via the client terminal were either typed in manually using the android device interface or using the default set of easy-buttons standard to the app UI.
You probably noticed that the there are two fields in the chart above with null values. The ProxmarkPro does not have the ability to access the firmware’s Mifare functionality required to read, write, or emulate our target HF cards without connecting to a client via USB. The only HF card type specifically accessible to the ProxPro in unchained mode is Mifare Ultralight. Unfortunately for the sake of this test, Mifare UL access systems are not as common on the open market, with most implementations being designed for large scale, high-volume applications such as hotel key cards, public transit fare cards, and customer loyalty tracking. That said, it can be safely assumed that the ProxPro would be able to read Mifare UL cards in a similar four to five seconds.
From this point in the test forward is where the ProxmarkPro really starts to show its limitations. With only three card formats accessible in unchained mode, reasearchers and redteamers will find themselves unable to use this tool in many live engagement scenarios. Although our array of RFID systems is in no way representative of the entire ecosystem out in the wild, neither does HID, EM4100, and Mifare Ultralight represent the most commonly used formats. The fact that the RDV4 provides full wireless connection to the client firmware makes it capable of performing the same basic read, write, and clone functions on almost any RFID system commercially available. With minor modifications to the command input, the RDV4 would perform this test with similar results against HID and Mifare Ultralight tags.
Emulating a Target Card
In this series of tests, we will determine how quickly the user can take the data previously read from the target card and begin emulating that card with each of our devices. Once the tag has been successfully read, neither the ProxPro nor the RDV4 require physical proximity with the card to emulate or clone that tag. In both devices, the function effectively results in the card data being loaded to temporary memory and ready to be used. This makes the length of time less crucial in this stage of the attack, however this section of the test does provide some insight into the relative difficulty in executing the function between the devices.
For the RDV4, you will need to make sure to note the tag ID /UID after reading the target card. This can be easily done by selecting the value from the client output and pasting it into the command input when needed. This intermediate step is not required with the ProxPro due to the function being specifically designed to automatically utilize the last card read or loaded. However, you will need to load the tag by name if you are recalling card data saved from a prior engagement, so make sure to note the name you save it under.
Video Clip 3 – Side-by-side video of Emulate

Figure 14 - ProxmarkPro and Proxmark3 RDV4 Card Emulation Time Chart

Figure 15 A - ProxmarkPro Card Emulation Display Reading in Unchained Mode
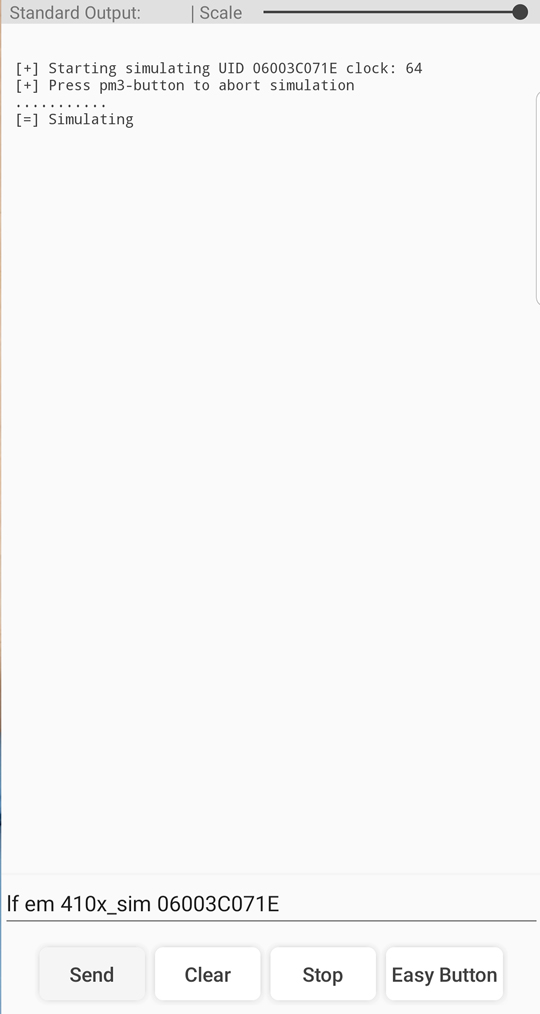
Figure 15 B - Proxmark3 RDV4 Card Emulation Client Input/Output via Android App
As discussed in the previous section, the ProxPro is only able to emulate the two LF card systems in our array. In any case, the transition from reading a card to replaying that card only requires pushing 3 buttons, resulting in a consistent four seconds to emulate each for the EM4100 cards. We can safely assume that emulating HID and Mifare UL cards would take a similar amount of time. Each attempt was verified successful by opening the target RFID lock with each of the devices.
Just as in the reading section of the test, there are minor differences in command inputs issued to the client for each of the card types. For all four of these cards however, the process can be essentially broken down to manually typing in the appropriate command and then either pasting or typing in the tag ID/UID of the target card. The exact inputs used for each target card can be found in the screenshots of figure 16 B. The average time taken to execute each successful emulation was 9.5 seconds.
Note the asterisk next to the value for the commercial HF reader – as stated earlier in the article, this system utilizes a hardened Mifare 1K card. The extra layer of security implemented in this card makes it impossible to merely read and replay the card data for reasons beyond the scope of this article. The RDV4 does have the ability to overcome this particular security measure with a few additional steps in the workflow, also accessible to the user through the client firmware. For a full demonstration on how this was accomplishes, read my tradecraft tutorial on cracking Mifare 1K using the Darkside and Hardnested attacks.
Yet again, the ProxPro proves quicker in execution over the RDV4 – albeit with several major caveats.
Cloning a Target Card
There are certain occasions where emulation of the target card will not be sufficient to bypass the RFID reader, such as in card systems that require dipping the card or in the case that card also serves as an ID badge. In these cases, the user will need to write the target card data to a blank/writable RFID card of the appropriate format. The process on either device is very similar to emulating a card with respect to work flow, and as such, does not require physical proximity to the target to execute.
According to the options listed on the menu and the device documentation on RC’s website, cloning target card data to a blank should be as simple as selecting the clone function from either the HID or EM4100 sub menu (it does not however list this functionality for Mifare UL). In practice, I was completely unable to successfully clone either of the two EM4100 cards used in this series of tests. Although the ProxPro was able to emulate both cards and bypass the reader, every attempt to clone that data to a blank failed.
The clone attempt was made on two separate T5577 blanks (the ones included in each devices’ kit) with no success. Initially thinking that this could be a peculiarity to the target cards, the process of reading and cloning was repeated with all remaining EM4100 tags used in the antenna range test. The ProxPro delivered the same failure message in every case. These failures were not taken at face value and were verified by attempting to bypass the reader with the failed clones.
I have not found any relevant documentation of this phenomena among other PromarkPro users in the community, so this inability to clone may be particular to our device due to some manufacturing defect or damage from use. I am unable to speak to whether the clone function requires any separate hardware components beyond that of emulating – short of that possibility the only explanation could be a problem with the device’s firmware. We will have to wait to see if this issue is resolved in the next firmware release (which is closed-source and only developed by Rysc Corp) or conduct the same test with another ProxPro in the future.
Video Clip 4 – Side-by-side video of Clone

Figure 16 - ProxmarkPro and Proxmark3 RDV4 Card Clone Time Chart in Seconds

Figure 17 A - ProxmarkPro Card Clone Display Reading in Unchained Mode
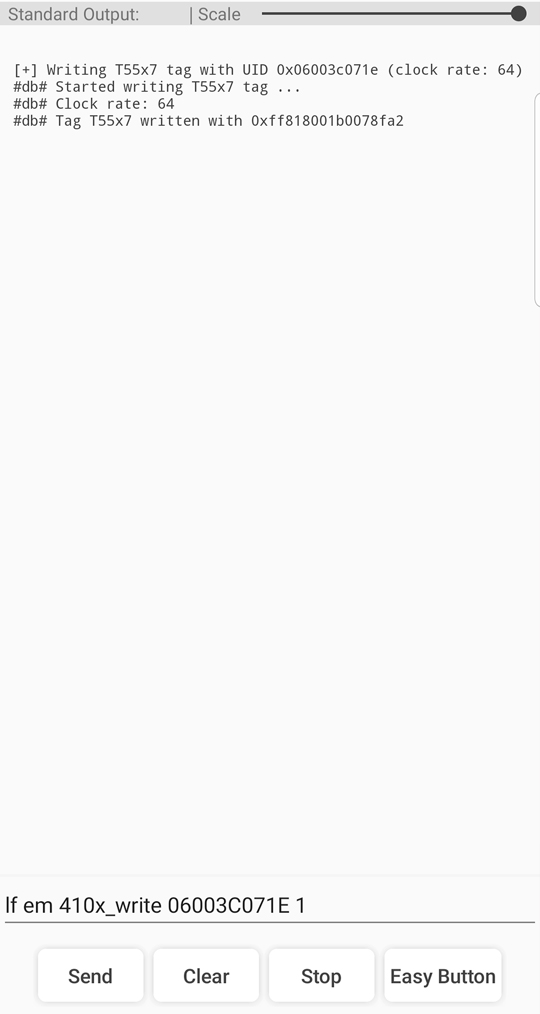
Figure 17 B - Proxmark3 RDV4 Card Clone Client Input/Output via Android App
The Proxmark3 RDV4 had no problem executing the write functionality for either of the two LF target cards, successfully cloning both the Rsyc Corp and RRG T5577 blanks with verified reader bypasses. The average time taken to execute the command and write to the card was 11.3 seconds against three out of the four target cards. The RDV4 is in fact capable of writing the data captured from the hardened Mifare 1K used with the commercial HF reader, however this requires a level of understanding of how these cards work that is beyond the scope of this article. There is a great article by Gavin Johnson-Lynn that is easy to follow without going too deep into the technical aspects if you really need to clone Mifare 1K cards after cracking them with the Hardnested attack right now.
For the first time in this series of tests, the Proxmark3 RDV4 provides a clear advantage over the ProxmarkPro in both raw speed and in range of capability. With each of the individual functions tested on each device, let’s move onto the main event for this trial: the complete card replay attack from start to finish.
Full Card Attack
Bringing the whole workflow together into a single test, we measured the time taken for both the ProxmarkPro and the Proxmark3 RDV4 to go from identification through emulation of the target card. The timer starts with the first button push/tap/type on the device and ends with confirmation of card emulation on the display/client output. The time was verified by successfully bypassing the reader with the device. The ProxPro was only able to compete in the LF category, as performing a read on either of the target HF cards is not possible, precluding it from being able to finish the trial.
Just for fun, we also ran an additional series of tests with RDV4 utilizing custom easy-buttons. Pre-programming the buttons does save some time compared to manually typing the commands on a touch screen, and has already crept into my daily usage of the device. In the spirit of this being a field test, we still manually retrieved and inserted the appropriate tag ID/UID into each command, as these would almost certainly be unknown values when beginning an engagement. Note that when using the easy button feature in this way, you will send an incomplete command to the client when it requires the addition of the retrieved tag ID/UID. This will cause the client to output the help file in most cases – simply ignore this, input the value, and resend the command to execute properly.
Video Clip 5 – Heads-Up Full Card Replay Attack Footage

Figure 18 - ProxmarkPro and Proxmark3 RDV4 Card Replay Attack Time Chart
It is clear from the results of this series of tests that the simplified interface of the ProxmarkPro provides the user with vastly greater speed when conducting a card replay attack in the field. With a mere eleven pushes on the direction pad, the ProxPro bypassed both LF readers in only 11 seconds each. As in our previous reading and emulating trials, it is reasonable to assume that the device would perform equally fast with both HID and Mifare UL cards as well. The ability to crank out the procedure with such a rapid succession of button pushes is impressive to say the least, and can probably even compete with custom LUA scripts designed to accomplish the same tasks automatically.
That said, the Proxmark3 RDV4’s performance comes in at an average of 35.6 seconds start to finish for the three non-hardened target cards. Although not factored into the test itself, when reviewing the footage of our run through of the low-end residential LF system, the actual time requiring the device to be in proximity of the target only amounted to 17 seconds.
For the commercial HF system utilizing the hardened Mifare 1K card, we modified the procedure to include the previously mentioned Darkside and Hardnested attacks required to fully decypher the card data. Start to finish, the best time achieved was 95 seconds, with less 70 seconds of required proximity to the target card. Again, refer to our full demo of this attack in the Proxmark3 knowledge base.
Analysis
ProxPro
From the perspective of raw performance in the time trials conducted, the ProxmarkPro is the clear stand out in quickly conducting card-side attacks in the field. In every individual function, the ProxPro out-paced the RDV4 by a factor of two. To boot, running the entire replay attack on both target LF cards totaled only 11 seconds, which was one quarter the time required when using the RDV4.
RC’s departure from the rest of the Proxmark3 community in the development of the ProxPro’s unique unchained mode and corresponding UI results in an incredibly fast and easy-to-use device. By standardizing its read, emulate, and clone functionality across the device and simplifying the work flow for these functions, the ProxmarkPro provides even the most novice user with the ability to quickly and effectively perform certain RFID attacks in the field right out the box. Even with the limited number of compatible card types, the sheer accessibility of this device should not be ignored. Performing these tests required no previous training or research to accomplish, unlike in the case of the RDV4.
PM3 RDV4
The Proxmark3 RDV4, while certainly not as easy to use, still performs extremely fast – with a maximum proximity time with the non-hardened target cards being at about 17 seconds when using the client terminal manually. Being able to consistently perform the replay attack over a majority of the card types used in the field more than makes up for the slight loss of speed when compared to the ProxPro. This becomes especially true once the user integrates LUA scripts into their workflow and replaces the tedious command inputs with automated scripts that get to work at the press of a single button (more on this in part three of this series). This of course requires a more advanced level knowledge and experience, which represents the only major disadvantage of the RDV4 in the field: it is not easy to get started with this device and will take a lot of research and practice to master.
Taking the time trial results in context with the differences in form factors and UI integration between the devices, the need for speed plays a greater role in the deployment options for the ProxPro over the RDV4. Because the ProxmarkPro itself must be visible to the user to navigate the UI and execute commands, every second that the device is in use is another second the user is exposed to scrutiny. Because the RDV4 externalizes this part of the workflow to a remote Android device, interaction with the device becomes almost invisible in any scenario where the user can freely use their smartphone, tablet, or netbook. This drastically reduces the reliance on speed alone when using the Proxmark3 RDV4 in live engagements. This covert but feature-rich interface is what makes the RDV4 so potent in the field.
Back To Field UtilityConclusions
In spite of its limitations, the ProxmarkPro by Rysc Corp delivers a useful array of RFID attack functions and is ready to use in the field right out of the box. This is the only Proxmark3 variant on the market that doesn’t require any interaction with firmware or client terminals to get up and running – the user literally requires no computer experience at all. As such, it is probably the best option on the market for any RFID researcher or redteamer with no experience in or inclination to learn Linux/command line computing.
However, it cannot be overlooked that the ProxmarkPro only offers read and replay functions for three out of the dozens of RFID tag formats in the wild. This hyper-specialization in use cases means that the ProxPro cannot adequately serve as a researcher or redteamer’s primary RFID toolkit. The device is more of a supplement to one’s toolkit for instances where the fastest and easiest tool for attacking HID, EM4100, and Mifare UL cards is required. In these scenarios where five to ten seconds makes the difference, the ProxmarkPro will shine. This is such a narrow range of applications however, that most professionals will likely find little if any use for it in live engagements.
The Proxmark3 RDV4 is not an easy tool to get started with. It requires significant time to setup and to learn the syntax of the 200+ different commands it is capable of executing without being tethered to a computer. The RDV4 by RFID Research Group is the only Proxmark3 on the market that can boast 100% utilization of the client firmware remotely, whether in the lab or a live engagement. It is more capable, more covert, and most importantly, the most supported device in the Proxmark community. This device will continue to grow with the latest research and attack techniques, as its open source firmware benefits from constant development by RFID luminaries such as Iceman, Proxgrind, and 0xffff.
In the next and final article of this three-part series, we will transition from the field to the lab, where we will be taking a deeper look at the firmware used in each device, and how that intersects with preparation of the device for specific engagements, implementation of custom features, and the future utility of the tool. Stay tuned and until then, remembered to keep it between the laws.


Cool article Ghost, have the proxmark pro, going to opt for the rdv4 instead due to the limitations of which you already mentioned – ultralight, hid, and em4100. need more than just that these days. would have been cool if they could code those in but no development in almost a year from Ryscc, sucks.