The proxmark3 is an open source / hardware device that was initially developed by Jonathan Westhues, which enables sniffing (both ways), reading, writing, emulating and cloning of RFID (Radio Frequency Identification) tags. Generally speaking, it’s basically a generic test instrument for HF/LF RFID systems.
This piece of hardware can do almost anything involving low (~125khz, 134 kHz) or high (~13.56 MHz) frequencies. It can act as a reader/writer. It can eavesdrop on a transaction between a legit reader and a tag. You can analyze the signal received over the air and you can also pretend to be a tag itself.
It is also capable of some less obviously useful operations that might come in handy for development work. We will write about these capabilities in some blog posts in the near future 😉
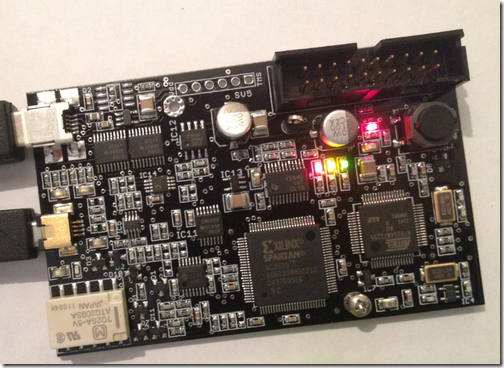
This is a close-up of a Proxmark3:
The largest IC is the FPGA; the ARM7 is to its right. The other chip is the ARM, which executes code out of flash, and can reprogram itself over USB. The USB connector is clearly visible at the top left, and the antenna connector is below it.
You will need two different antennas in order to deal with Low and High frequencies.
High frequency antenna:
Low frequency antenna:
If you’re looking for the latest code to deal with this beauty, browse here: https://github.com/Proxmark/proxmark3. You’ll also find out that this is a VERY active community, so, be prepared to have fresh updates every week. You’ll need to update the Proxmark3 with the boot rom, fpga and arm image, and then call the client.
Get ready to fail a couple of times, and read a lot. The very best resource is the community forum, which is located here: http://www.proxmark.org/forum/index.php. You can register for free, of course, and start reading all the stuff shared there.
2018-01 Note: This article covers the original design of the proxmark3, which was created several years ago. The core information is still valid, but the new device looks completely different and has more features.