Now that we own the keys of a Mifare Classic card, we can move onto cloning them. Just as a quick reminder, the steps to crack the keys were: proxmark3> hf mf mifare proxmark3> hf mf nested 1 0 A XXXXXXXXXXXX d If you take a look inside the current folder where the client is […]
Category Archives: Proxmark
Knowledge Base Table of Contents - Proxmark
Firmware notice: In case you didn’t notice, Proxmark3 source code has moved to GitHub! So, you have to pull the stuff from here: https://github.com/Proxmark/proxmark3. The good news are that update instructions are the same! So grab a fresh copy of the stuff and recompile, update the firmware, and you’re on the new wave. If you […]
In this post, we’re going to review the update procedure just in case you want a little refresh on this and then we’re going to move into the world of Low Frequency RFID, sniffing, cloning, emulating, EM4X tags, and the fabulous T55x7 card. Ok, let’s start with the update procedure: $ make clean $ export […]
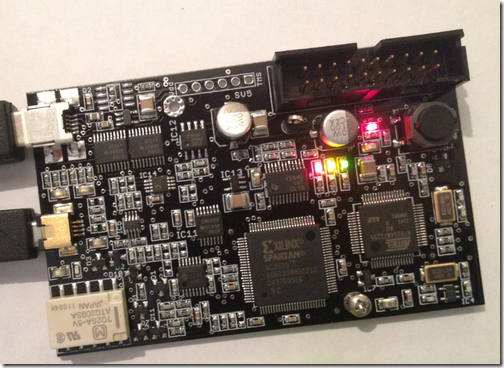
So now you’re a proud owner of a Proxmark3 device and you want to know where to start, right? As we mentioned in the previous post, the best way to start is to dig up the Proxmark3 forum posts, be ready to register and start searching. In this blog post, I’m going to guide you […]
The proxmark3 is an open source / hardware device that was initially developed by Jonathan Westhues, which enables sniffing (both ways), reading, writing, emulating and cloning of RFID (Radio Frequency Identification) tags. Generally speaking, it’s basically a generic test instrument for HF/LF RFID systems. This piece of hardware can do almost anything involving low (~125khz, […]