Powerful and Pocket-Sized NFC Emulation and Analysis
The Chameleon Tiny Pro by RFID Research Group
The Chameleon may have began its career in infosec as a breadboard hot glued to a coffee mug wrapped in copper wire, but ever since the first official build of the device in 2013, it has become a very popular and powerful addition to the toolkit of pentesters and researchers alike. Originally developed by Kasper and Oswald (aka: KAOS), the device was intended to serve as a field-capable NFC and RFID tag reader, emulator, and sniffer to analyze the security of these systems in the wild. Thanks to the continued development of the project in the open source community, the Chameleon has seen several major improvements in both hardware design and firmware capabilities.
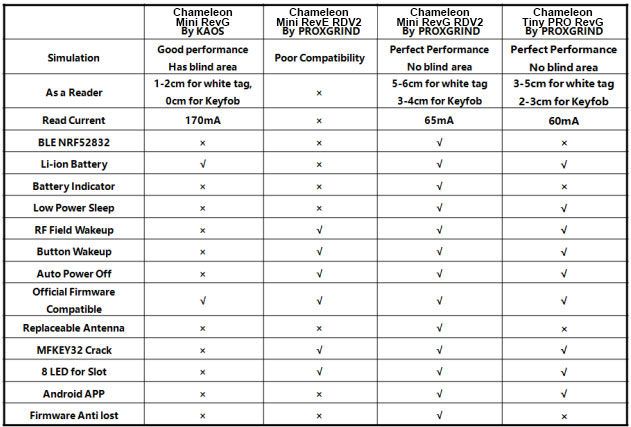
Although RRG had already made substantial hardware and software improvements to the project in the form of the RevG in 2019, the Chameleon Tiny managed to substantially simplify and minimize the hardware, introducing a new key fob form factor. Although this iteration was missing the wireless functionality, the Pro version of the device now includes an on-board BLE module allowing for wireless connection to the client software just like the RDV2, making it ta great choice for the field.
Covert Form-Factor
The Chameleon Tiny is by far the smallest variation of the device currently on the market – at only a quarter of the size of the Chameleon Mini RDV2, it is smaller than most automotive key fobs. It features a decorative and functional board design with a durable epoxy dome protecting the device from wear and tear in the field. The included loop makes it easy to attach the device to a lanyard or key chain.
Beyond the advantages provided by its physical size and design, the ability to control the device remotely from an Android App via Bluetooth makes deployment of the device even more flexible in live engagements. By eliminating the need to physically interact with the Chameleon Mini while in use and opening up the full capabilities of the firmware thru the App, a wider range of attack techniques typically reserved for the lab can now be performed covertly in the field.
Android App
The primary benefit of the Chameleon Tiny Pro by RRG is the custom Android App that allows you to control the device remotely with a few taps on your smartphone, tablet, or netbook. The application provides a simplified UI that lets the user program card data to the 8 different card slots, customize the functionality of the device buttons, and view live readings when sniffing traffic to name just a few of its capabilities. Just as in the Proxmark3 RDV4, the firmware required for use with the Android App is a custom fork available directly from RRG in both pre-compiled and source formats. The device is however fully compatible with the official project firmware.
For more information on setting up and using the device with the Chameleon App, check out our article or read the documentation on RRG’s GitHub page.
Scenarios/Usage
While the Proxmark3 was designed specifically for research in RFID proximity card systems, the Chameleon was developed for use in NFC applications of RFID technology. This does result in a substantial amount of overlap in functionality between the two devices, especially with respect to the ISO14443A RFID chips used in Mifare-type cards. In this respect the Chameleon Tiny Pro is more versatile and easy to-use-version of the Promxark3’s standalone mode for HF RFID tags – the device is not compatible with LF cards like HID, EM4100, T5577, etc.
One of the primary distinctions between the Chameleon Tiny Pro and other RFID tools like the Proxmark3 is the ability to easily program and run pre-scripted commands from the device at the push of a button. The device also requires a much lower threshold of experience in RFID to get started with compered to the PM3, allowing the user to implement attacks in the field with much less effort and setup time. This has made the Chameleon uniquely valuable in the field as a quick and stealthy way of capturing, cracking, and replaying encrypted card data in a live engagement.
The Chameleon Tiny amplifies all the best qualities of the device by making it both completely wireless, but also very easy to reconfigure the device on the fly during a live engagement. The simplicity of the UI makes responding to a change in strategy and the implementation of a variety of attack techniques as simple as pressing a few buttons on your Android device while within BLE range of the Chameleon. The range of capabilities combined with the price point also makes it an ideal starting place for newcomers to RFID research/pentesting.
This introduction only scratches the surface of field utility the Chameleon Tiny Pro by RRG provides its user and definitely should be considered a must-have for any RFID researcher or redteamer’s toolkit. We will continue to explore the capabilities of this device through tutorials and tradecraft – including how to set the device up with the Android App and programming the device to crack Mifare Classic cards in the field. For more information on how to setup and use the Chameleon Tiny, make sure to check out the rest of the articles in this series.