The most common use case for the Chameleon Tiny Pro is the cloning and storing of Mifare tag UIDs with the end goal of bypassing a target reader through emulation. Surprisingly, many systems in the wild do not employ any of the security features supported by the tag, which makes the device incredibly useful for a variety of engagement scenarios. Cloned tag data is stored on any of the Chameleon’s 8 card slots for easy recall and replay of UIDs, which is usually done in the field through the default standalone functions provided by the A and B buttons on the device.
The Chameleon Tiny Pro by RFID Research Group make this workflow even easier via the Android App, providing push-button management of your device’s card slots directly without fiddling around with the tiny buttons and LEDs on the physical device (in fact, it can be hidden in your pocket for the entire process). The tags can be cloned, stored to, and recalled from the Android file system as well, extending the size of your digital key chain to thousands of UIDs. The app also allows the user to quickly configure a given slot for more advanced functionality, such as sniffing and reader modes. In this article, we will walk through the process of cloning a tag’s UID and configuring the function of the card slots on your Chameleon Tiny Pro.
Cloning Tag UIDs to a Card Slot
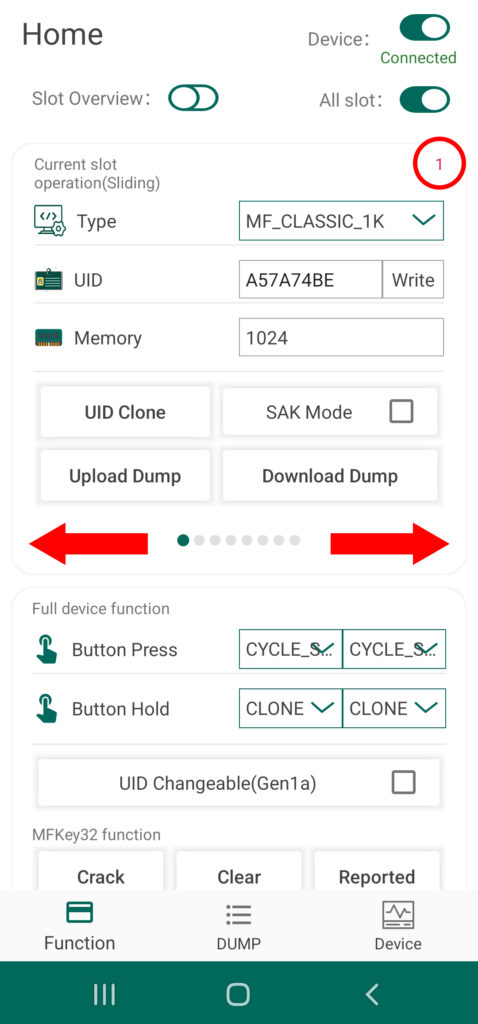
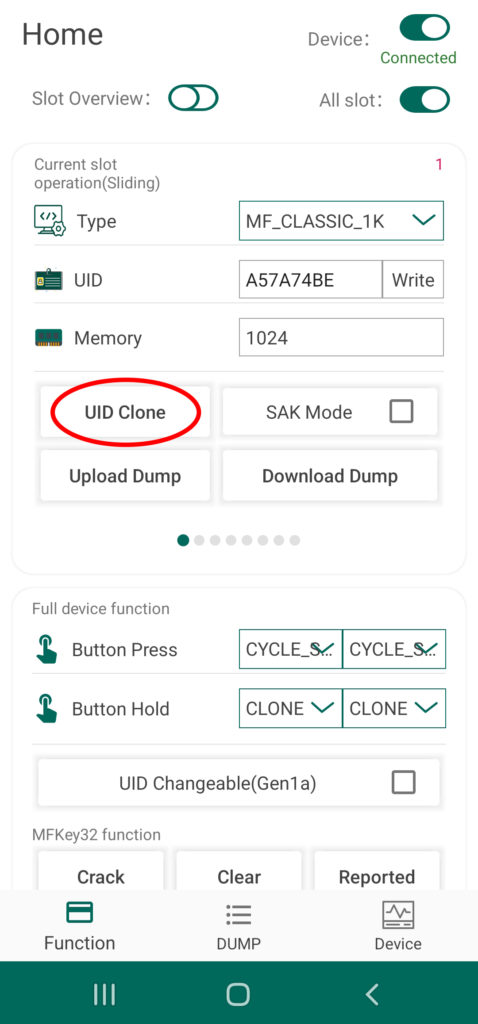
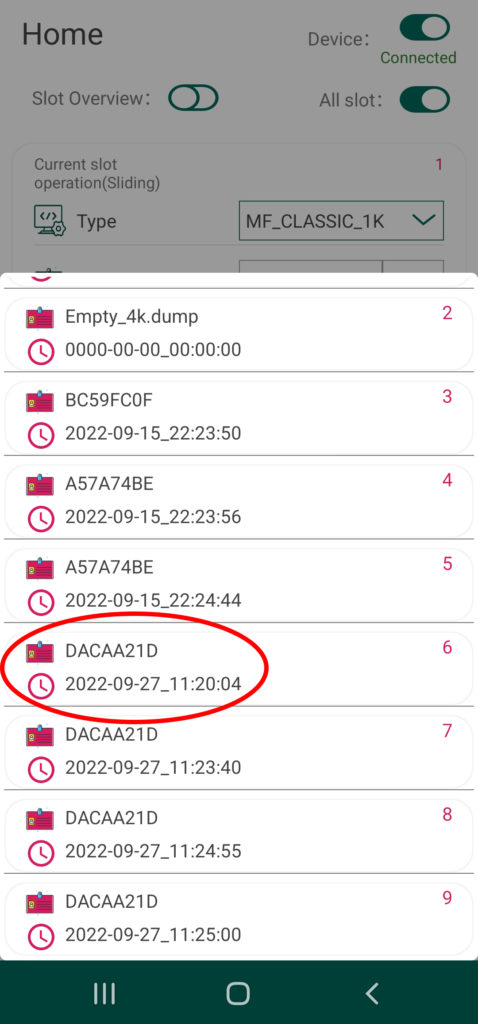
From the Chameleon Android App by RRG, simply connect to you device via Bluetooth and navigate to the Home Screen of the UI. From here, you can quickly and easily toggle between the eight different card slots by swiping left or right of the section of the screen labeled “Current Slot Operation”. The current slot number is indicated by a red numeral in the upper right hand corner as well as a tray of small circles at the bottom of this section. To clone a target tag’s UID to your device, simply swipe to the desired slot number, place the card over the Chameleon’s antenna, and tap the button called “UID Clone”
When ever the device is set to this specific slot, your Chameleon Mini Tiny Pro will emulate this unique tag ID in the presence of a card reader. By default, the Chameleon’s standalone mode is configured to cycle through the cards via the A and B buttons on the physical device – for more information about standalone mode functionality, read this article of the series.
Storing and Loading Tag Data from Android Device Memory
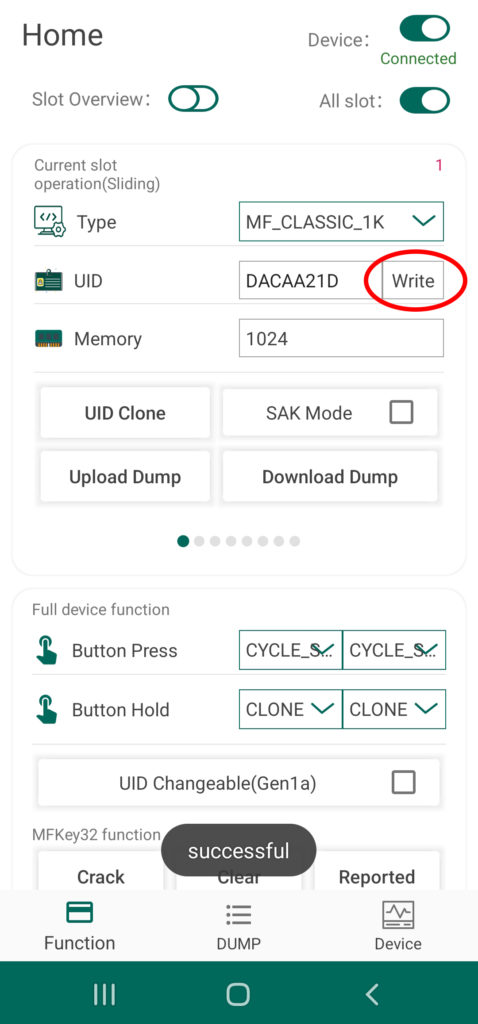
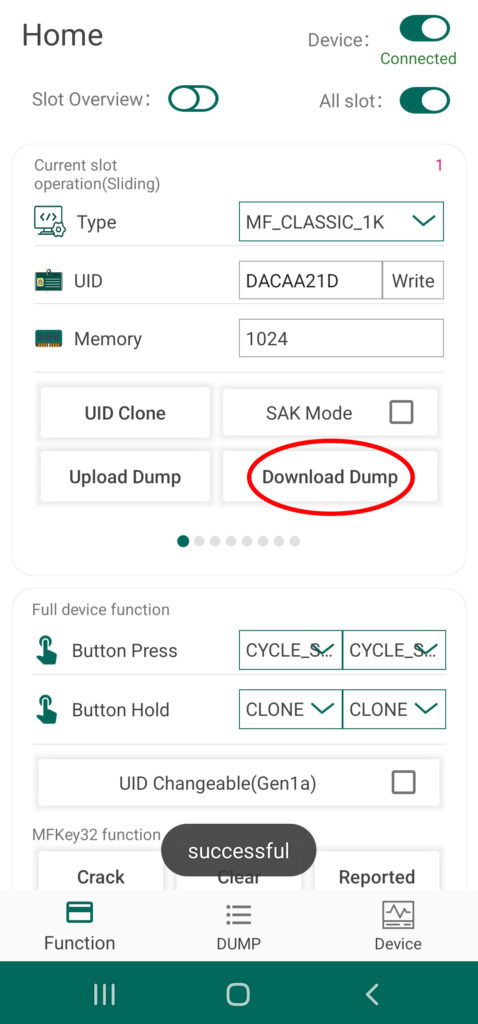
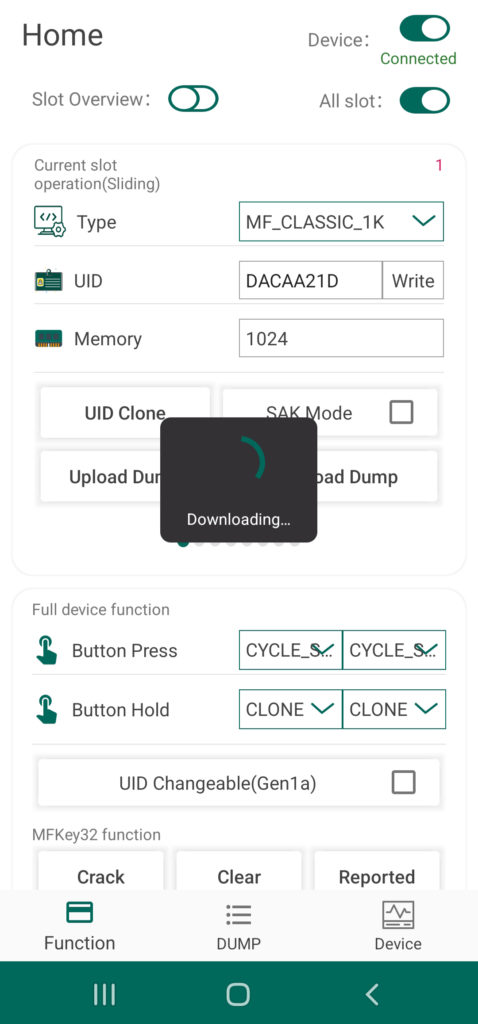
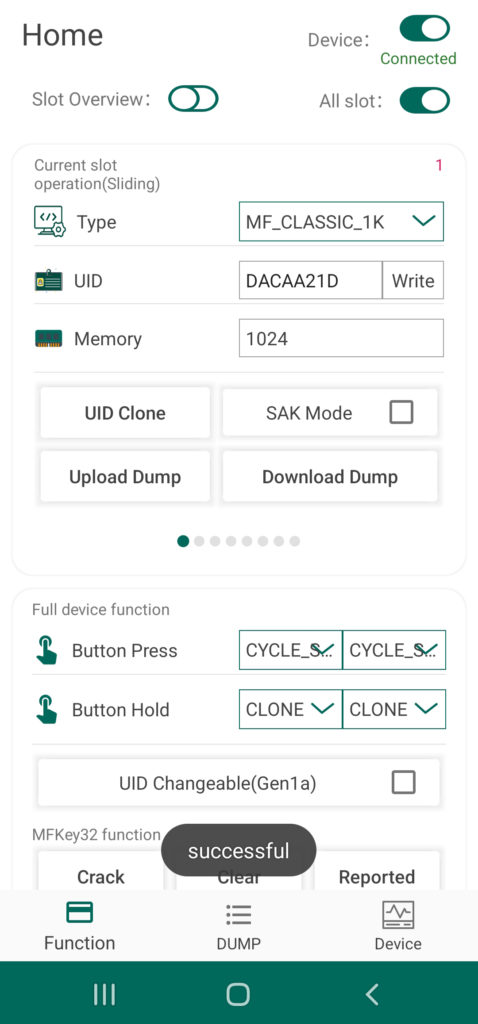
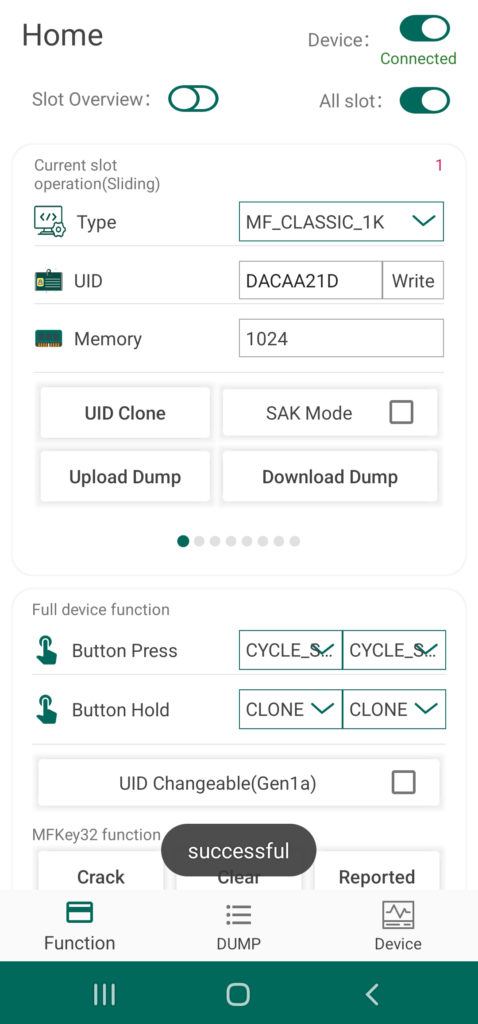
Beyond the eight card slots included in the Chameleon’s onboard memory, any tag UID or tag data currently stored to the device can be uploaded to the Android system’s storage drive and vis a versa. This extends the capabilities of the Chameleon Tiny Pro to provide an essentially limitless number of keys on demand. To save a UID via the app, simply Clone a tag following the last procedure and then tap the button labeled “Download Dump”. The tag’s UID as well as any other data you were able to scrape will now be accessible via the Dump screen of the UI.
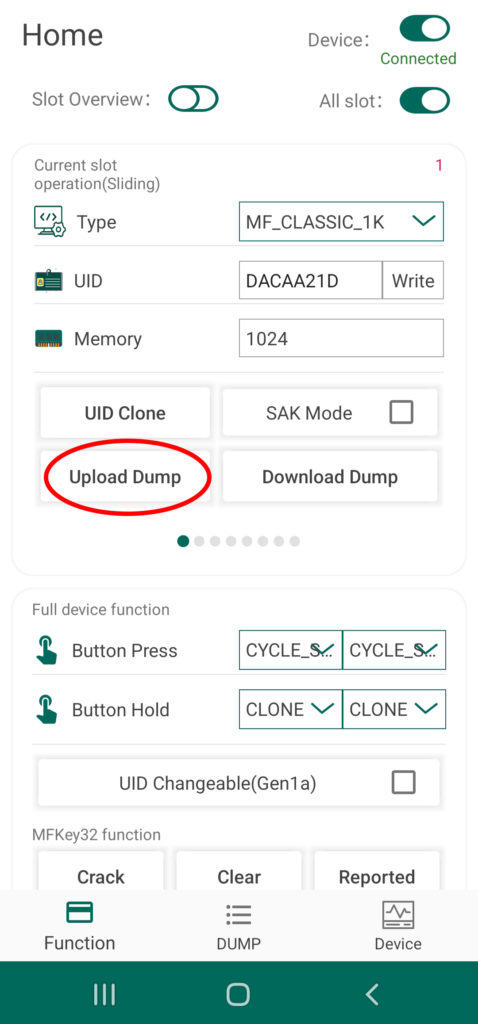
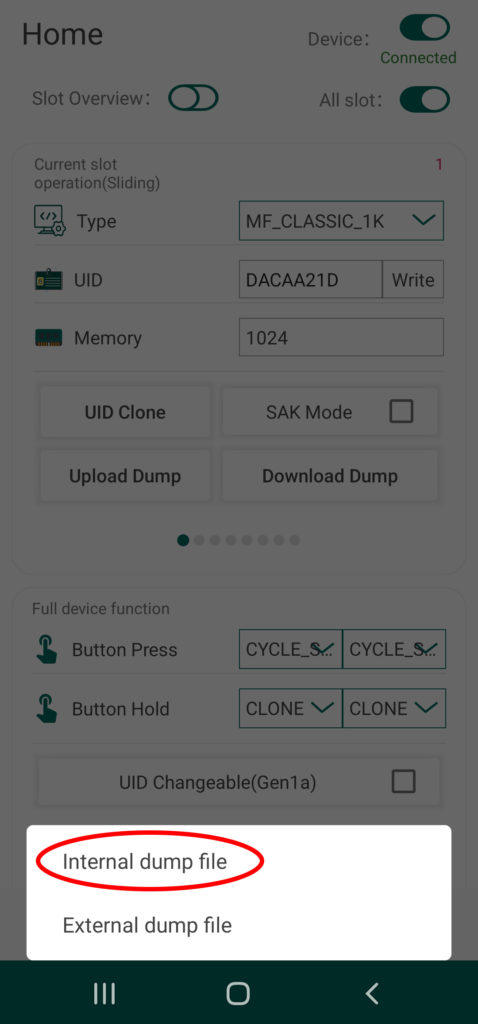
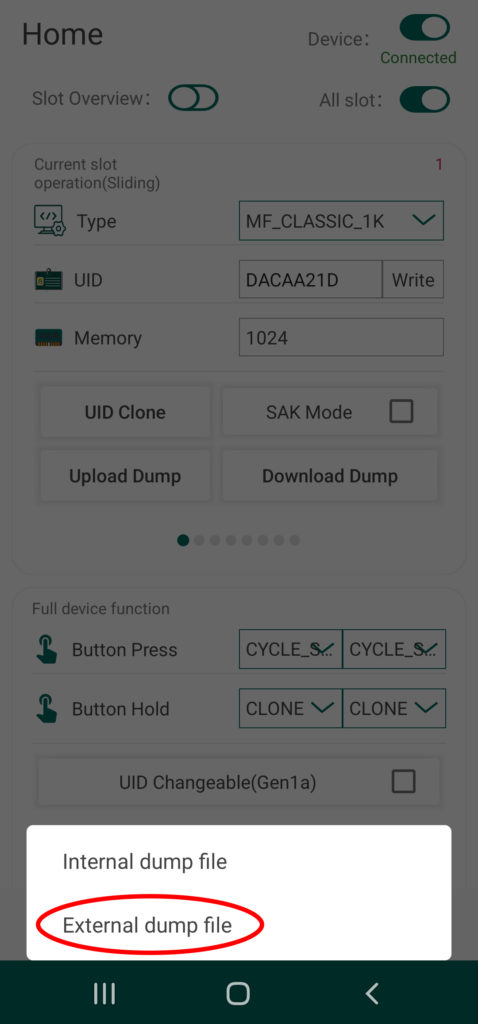
You can also transfer tag dumps from the app to a card slot on your Chameleon by taping the button called “Upload Dump”. You can either select from internal or external, with the first loading up a menu of files currently saved to the app’s directory, and the second option allowing you to load dumps from other sources. The selected file dump file will be automatically stored to the designated slot of you device.
This is a very useful feature for transferring tag data between different software platforms when conducting more advanced research. Workflows that combine the Proxmark3 RDV4’s capabilities with the Chameleon for example, can now be done quickly and discreetly on your smartphone. For more information on Mifare cracking, check out this article in our PM3 knowledge base.
Programming Slot Functions
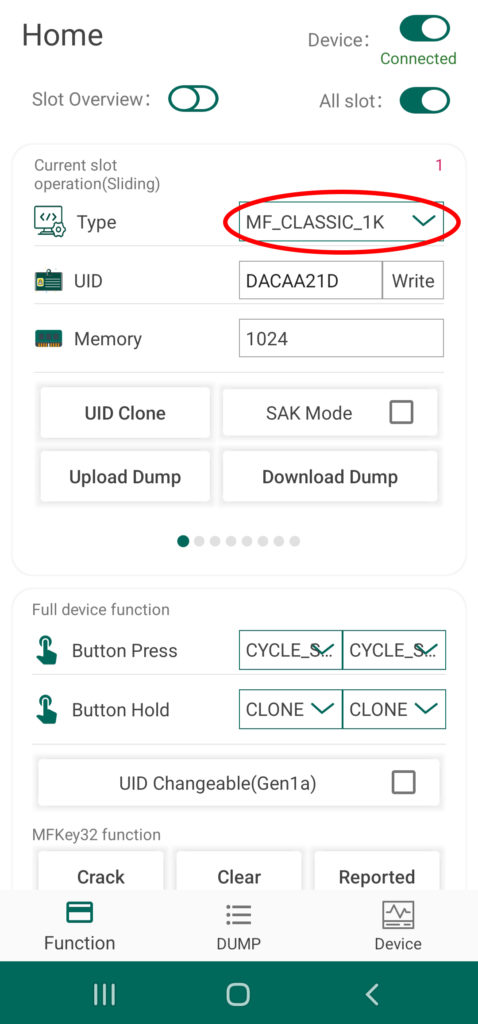
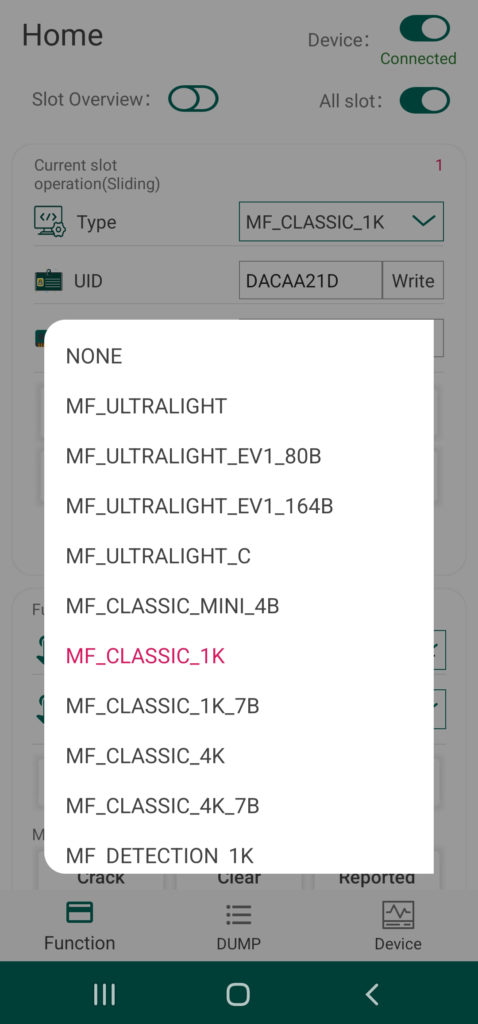
The primary operation performed by card slot on the Chameleon is the emulation of a particular tag type or protocol. This operation is automatically set to the appropriate selection required to emulate the tag that has just been cloned, and thus is not really useful in a lot of cases. However, this operation can be manually set by using the drop down menu labeled “Type” at the very top of the UI section called “Current Slot Operation” to access functionality other than mere tag emulation. This includes a couple of sniffing modes and mode that allows some advanced interaction with tag readers.
| Slot Functionality | |
|---|---|
| Label | Description |
| NONE | Card slot has no function |
| MF_CLASSIC_1K | Emulate Mifare Classic 1K 4 Byte UID |
| MF_CLASSIC_1K_7B | Emulate Mifare Classic 1K 7 Byte UID |
| MF_CLASSIC_4K | Emulate Mifare Classic 4K 4 Byte UID |
| MF_CLASSIC_4K_7B | Emulate Mifare Classic 4K 7 Byte UID |
| MF_DETECTION_1K | Read Mifare Classic 1K |
| MF_DETECTION_4K | Read Mifare Classic 4K |
| ISO14443A_SNIFF | Sniff ISO14443A communication between a reader and a card |
| ISO14443A_READER | Emulate ISO14443A reader when communicating with a card |
| MF_ULTRALIGHT | Emulate Mifare Ultralight |
| MF_ULTRALIGHT_EV1_80B | Emulate Mifare Ultralight EV1 80 Byte UID |
| MF_ULTRALIGHT_EV1_164B | Emulate Mifare Ultralight EV1 164 Byte UID |
| VICINITY | Emulate Vicinity |
| ISO15693_SNIFF | Sniff ISO15693 communication between a reader and a card |
| SL2S2002 | Emulate SL2S2002 |
| TITAGITSTANDARD | Emulate TiTag Standard |
| EM4233 | Emulate EM4233 |
It is beyond the scope of this article to cover the the sniff and reader functions, as they are most useful in the context of more advanced attack techniques and research workflows. The reader function, for example, is an important part of the infamous MFKEY32 attack. Stay tuned for our upcoming demo of this Mifare hacking technique!
This of course only represents the most basic capabilities provided by the Chameleon Tiny Pro. For more information on how to setup and use your Chameleon, make sure to check out the rest of the articles in this series. If you don’t already have one, visit Hacker Warehouse, the exclusive North American retailer of this and other awesome RFID devices from RRG. Until next time, keep it between the laws and between the LOLs.